Content and Location Security
Content Security
Content security, also referred to as intellectual property security, means providing security for the contents of, or intellectual property within, a file.
To explain further:
With some file types, once the file is opened, the full content is visible and accessible, e.g. a simple text file.
With other file types, however, the file contains various information in the form of 'objects' or 'containers' within the file. It is thus possible to allow users access to, and use of, a file, yet keeping at least some of the content secure within the file. So it is with Excel, and, in particular, the security system as implemented in Spreadsheet Sentry.
The native Excel content protection systems are all crackable, rendering the object protection system virtually useless. Spreadsheet Sentry, however, brings a whole new approach to spreadsheet security, providing a robust security system, independent of Excel, yet operating transparently within the normal Excel operating environment.
At encode time, the Spreadsheet Sentry encoder encrypts the formulas within the cell, using a strong, internationally-accepted encryption algorithm. At run-time, on demand, the formula is loaded in to a secure memory space, decrypted, calculated, and then discarded – all within a few micro-seconds. Thus, the original formula is never accessible to users – authorized or not.
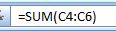
For example, this plain-text formula:
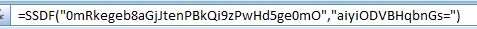
might be replaced by this encrypted formula:
Location Security
The concept of 'location security' is that a file should be 'location aware', and, depending on the circumstances, allow itself to be used, or not.
In its native format, an Excel file has absolutely no 'location awareness'. This means that the most valuable or confidential spreadsheet once copied from its original (possibly network-secured) location, has no defense against being copied to, or run from, other locations.
Spreadsheet Sentry, however, via the run-time Client Excel add-in, and the (owner selectable) security parameters assigned at encode time, has the ability to ascertain whether embedded security parameters are met, and hence whether the spreadsheet is allowed to be used.
While network access restrictions may be used in conjunction with Spreadsheet Sentry, these are then not the only security system, i.e. the embedded security requirements automatically travel with the spreadsheet – for evaluation and approval each and every time, wherever the file is attempted to be used.
See also:
Benefits of using Spreadsheet Sentry
Limitations of native Excel protection